Understanding the Basics of Cybersecurity
Our world is swimming in online threats, and nobody wants their stuff hacked or stolen. This cybersecurity for beginners guide is for people who want to prevent themselves from becoming victims like those who come to me while I’m at work.
What’s cybersecurity and why’s it a big deal these days
Think of cybersecurity as a digital bodyguard. It’s all about keeping nosy strangers out of your digital space, stopping cyber sneak attacks, and keeping your private info under lock and key. The threats are getting smarter and more frequent too. From lone folks to big companies, cyber risks are everywhere. If it goes wrong, you might lose money, have your data nabbed, or trash your good name.
Meet the usual suspects: common cyber threats for the average internet user
- Phishing: It’s like digital catfishing. Sneaky emails or messages pretend to be real to swipe your personal info. They often look like they’re on the level but are all about getting your passwords or credit card numbers (OCC).
- Malware: Consider it software with a vendetta—viruses, worms, or trojans that mess with your gadgets and grab data without asking.
- Ransomware: This crappy software locks you out of your stuff and demands cash to let you back in.
- Man-in-the-Middle (MitM) attacks: Imagine someone eavesdropping on a private convo and sometimes changing bits of it without you knowing.
Getting wise to these threats means you’re better armed to stay one step ahead and secure your stuff.
The CIA triad: Confidentiality, Integrity, and Availability (Not the dudes in suits)
The CIA triad isn’t about secret agents, but it’s just as crucial in the cybersecurity world. Here’s the lowdown:
- Confidentiality: Only letting the right peeps in on the secret. Think of encrypted locks and secret passwords.
- Integrity: Keep that information straight and true. No funny business with your data is allowed with checking tools and hash functions.
- Availability: Your info must be available when you need it. Keep those systems running smoothly with updates and plan Bs for disasters.
| Principle | Tell Me More |
|---|---|
| Confidentiality | Hide your stuff from prying eyes with locks like encryption and password controls. |
| Integrity | Make sure your data is all legit and untouched with integrity checks and hash functions. |
| Availability | Keep things working and accessible with regular updates and solid backup plans. |
Check out more of how this works in our piece on keeping your identity safe.
Keeping your head above water in today’s wired-up scene means knowing your stuff about cybersecurity. Understanding the boogeymen of the cyber world and cluing into the CIA triad keeps your digital space locked down tight. For even more street smarts, peek at our tips for safe browsing practices and email security tips.
Essential Password Security Practices
When swimming in the sea of online security, pulling a strong net around your passwords is a biggie. It’s not Sherlock-level detective work, I promise! Just by beefing up your password game, you can punch cyber gremlins right where they count.
Creating Strong, Unique Passwords That Are Actually Memorable
Even your grandma’s cookie jar has a lock, so why not your passwords? Mix it up with a dab of uppercase, a splash of lowercase, a sprinkle of numbers, and a dash of symbols. Be bold—aim for 15 to 20 characters. According to folks at Avast, this kind of strength sends brute-force attacks packing.
Who wants to remember “Fh#92gB6^zWs”? Spare yourself the brain sprain and go with a passphrase instead. Picture this: “CorrectHorseBatteryStaple!”—secure yet strangely memorable.
| Character Type | Example |
|---|---|
| Uppercase Letters | A, B, C… |
| Lowercase Letters | a, b, c… |
| Numbers | 1, 2, 3… |
| Symbols | !, @, #… |
Need extra guidance? Check out our how to create strong password guide, it’s packed with goodies!
Why Password Managers Are Your New Best Friend
Sick of writing down a million passwords, only to forget the one you need? Enter: password managers. They’re like your nerdy best bud who remembers all the important stuff for you. These handy helpers store and auto-fill those head-scratching passwords without a hitch.
LastPass, 1Password, and Dashlane are a few of the valedictorians in this class. Curious? Dive into our best password manager selections and find your match.
The Importance of Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) is like adding an extra deadbolt. Not only do you need to remember your password, but you’ve got to verify with that cheeky text message or app notification, too. Google Authenticator or a quick SMS can save the day when cyber thugs come knocking.
Curious about what’s under 2FA’s hood? Explore what is 2FA and turn it on like a champ.
Common Password Mistakes to Avoid
Don’t be one of these password sinners:
- Captain Obvious Passwords: Goodbye to “Password,” “123456,” and “Qwerty.” No brainer, right?
- Personal Tidbits: Keep your own name, birthdate, and any Sherlock-level clues out (Webroot).
- Repeating Yourself: One password to rule them all equals one key for every door. Beware (Webroot).
- The Shorty: Any password less than 12 characters? Time for a makeover.
- Playing Connect-the-Dots: Patterns like “abcdef” or “654321” just won’t cut it.
Reinforcing these password boundaries lets you bounce hackers off your harbors. Curious for more wisdom on shielding your bits and bytes? Cruise through our email security tips and learn how to secure your smartphone—they’re packed with goodies too!
Protecting Your Personal Data Online
Right now, keeping what’s yours, well, yours, is mega important. Let’s chat about what sneaky traps lurk out there, trying to snatch your deets, and how you can outsmart ’em with some savvy tricks.
Understanding What Personal Information is at Risk
So, what’s on the line? It’s everything from your name and home address to the big guns like your social security number, bank info, and even those health records you’d rather keep private. Cyber bad guys are known to target this stuff for their shady deeds, like stealing identities or bagging your cash. Watch out for phishing – it’s a big favorite of theirs. Those phony emails claiming to be your bank or a government agency? Yeah, don’t fall for it! The Office of the Comptroller of the Currency has all the horror stories.
Safe Browsing Habits and Best Practices
Want to keep snoopers out of your business? Adopt browsing habits that are more secure than a vault.
- Steer clear of dicey links and sketchy ads.
- Always double-check those URLs to make sure you’re where you really wanna be.
- Get yourself some trusty antivirus software like best antivirus software to sniff out and zap any threats.
- Don’t sleep on those system updates! They patch up the holes hackers love (CISA).
Using VPNs and Secure Networks
Here’s a pro tip: arm yourself with a Virtual Private Network (VPN). It adds a cloak-and-dagger level of security that even the sharpest hacker struggles to crack. VPNs are your best pal, especially on sketchy public Wi-Fi. If you’re in the market for one, peek at our piece on the best VPN services.
| Action | Benefit |
|---|---|
| Using a VPN | Scrambles your data and puts a mask on your IP |
| Connecting to secure networks | Slashes the chance your data’s going anywhere it shouldn’t |
| Avoiding public Wi-Fi | Shuts down any unauthorized snooping |
Want to stay safe while sipping coffee at your local café? Skim through our guide on how to use public Wi-Fi safely.
Privacy Settings on Social Media Platforms
Social media is fab, but it’s also a nosy player’s paradise. Keeping your information safe means playing it smart with your privacy settings. They collect information like it’s going out of style, so lock it down!
- Switch to private profiles to keep a nosey neighbor out.
- Keep your life updates low-key and sparse publicly.
- Give app permissions a once-over regularly – tighten the reigns if necessary.
Check out our walkthrough on social media privacy settings for the nitty-gritty on these.
Master these tricks and you’ll be a privacy pro in no time.
Email Security and Phishing Prevention
How to Spot Phishing Emails and Scam Attempts
Ever get an email that doesn’t quite sit right? That might be a phishing attempt—cyber trickery at its finest. These emails usually wear a mask, pretending to be from trustworthy places, trying to snatch your info. They often scream urgency, hoping to catch you off guard with a splash of panic or intrigue, making you drop your guard just long enough to slip your info or click on something dangerous (OCC).
Watch out for these telltale signs of phishing emails:
- Urgent requests: If they’re yelling at you to ‘act now’ or else, question it.
- Strangers in the inbox: Random emails asking for your sensitive details? Red flag.
- Playing with emotions: They’re crafted to make you curious or scared, sometimes even tugging at your heartstrings (Cofense).
- Shady links: Check those URLs—crooks love making fake sites look real.
Curious about more ways to spot these sneaky emails? Check our guide on how to identify phishing emails.
Here’s a personal example from my own email address.
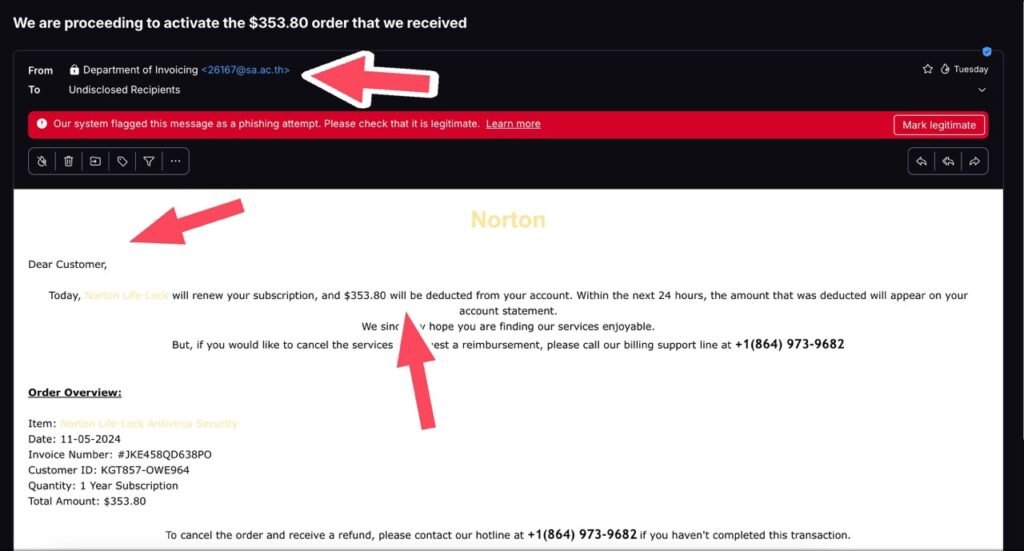
Safe Email Practices and Habits
Dodge those cyber bullets by keeping these smart email habits:
- Double-check senders: Confirm where the email’s actually from—it’s worth your time.
- Hover, don’t click: A quick hover over links shows their true path—know before you click.
- Handle attachments like they’re hot: Unless you’re expecting them, don’t open attachments willy-nilly.
- Activate spam filters: Use email filters to prevent pesky phishing attempts. For more handy tips, visit our email security tips.
What to Do If You’ve Clicked on a Suspicious Link
Oops! Clicked something fishy? Don’t sweat it, just act fast:
- Go offline: Cut the internet to stop any data leaks.
- Run a scan: Use your best antivirus software to sweep your device for nasties.
- Switch up your passwords: Protect any accounts you think might be hit.
- Keep an eye on money matters: Look for unexpected charges.
- Sound the alarm: Contact service providers if there’s a breach.
Want to know other signs that your computer’s been meddled with? See our guide on signs of computer hack.
Setting Up Email Filters and Security Features
Spam got you down? Put email filters to work:
- Spam filters: Let built-in filters do their thing—shift those sin-bin emails into the spam folder.
- Make your own rules: Craft filters with keywords or sender details.
- Rev up security features: Upgrade with best email security tools to fend off phishing and other cyber baddies.
Check your email provider’s settings for more info on setting these up. For a fuller picture, visit our section on email security tips.
By playing it smart and recognizing these signs, you’re doing your part to keep phishing cons at bay. Stay sharp!
Securing Your Devices
If you’re keen on keeping digital drama out of your life, locking down those gadgets is a solid move! Think of it like putting the best security on your front door, except this door’s to your online world. Let’s break down how you can armor up your devices without turning ’em into a paranoia marathon.
Essential Security Software and Tools
Alright, so you’ve got tech goodies, but what about tech baddies? Here’s your digital justice league:
- Antivirus Software: Think of it like a digital bouncer, weeding out malware troublemakers. Don’t skip our roundup of the top antivirus champs.
- Firewall: This is your not-today-satan shield for lurking online nasties. A top-notch firewall is so underrated.
- Anti-spyware: This program monitors sneaky peepers trying to nab your data. However, you have to be careful because certain anti-spyware programs have a lot of your data in their hands. Check their features thoroughly.
- Password Managers: Who can remember a gazillion passwords? Let a password manager handle that memory stress.
- When you want to keep your browsin’ under wraps, read all about top VPN picks.
| Security Tool | Function |
|---|---|
| Antivirus Software | Kicks malware off your digital lawn |
| Firewall | Keeps online creeps out |
| Anti-spyware | Stops data snoopers in their tracks |
| Password Manager | Juggles your password puzzles effortlessly |
| VPN | Sneaks your browsing habits past prying eyes |
Keeping Your Systems and Apps Updated
Think of updates like your tech’s personal trainer. Suggested by the folks at CISA, here’s why updates shouldn’t be a snooze button affair:
- Security Patches: These block hackers like noise-canceling headphones block annoying sounds.
- Performance Improvements: No more sluggish tech; updates keep everything breezy.
- New Features: Added bonuses that often come with security perks.
To avoid headaches like outdated tech posing risks (CISA), stay hip by checking for updates often.
Mobile Device Security Basics
Want to keep your mobile pals safe from nosy Normans? Here’s how you do it:
- Use Strong Passwords or Biometrics: Beef up with a memorable password or let your thumbprint do the talkin’.
- Install Security Apps: A solid security app keeps baddies at bay. Peek at our list of top mobile security apps.
- Regular Backups: A little ‘data insurance’ never hurts — here’s the spiel on data backup strategies.
- Avoid Public Wi-Fi: It might be free, but coffee shop Wi-Fi isn’t always cost-friendly. Check out our tips for cool but cautious surfing here. If you must use public Wi-Fi, use it with a Virtual Private Network (VPN), and you’re golden.
| Mobile Security Basics | What to Do |
|---|---|
| Use Strong Passwords | Tap in tough passwords or biometrics |
| Install Security Apps | Build a fortress around your phone |
| Regular Backups | Never lose sleep over lost data again |
| Avoid Public Wi-Fi | Keep your surfing exclusive |
Backup Strategies to Protect Your Data
Let’s talk backups — the unsung heroes of ‘whoops, my bad’ moments. Here’s how you keep your data snuggly safe:
- Cloud Storage: Dump your data in the cloud, where weather ain’t a bother. Get tips on locking it down here.
- External Drives: Like a vault you can stash in your bag, keep backups regular.
- Automated Backups: Set it and forget it — this one’s all good against data-doomsday.
Mix it up a bit with these methods, and you’ve got a pants-tight plan against unexpected data fiascos. Feel like a security smarty? Check out our stories on phone fortification and how to mix homey vibes with security ninja moves here.
Safe Internet Browsing Practices
Keeping your surfing on the web secure can save you from a lot of headaches. Here’s how you can protect yourself while you’re online.
Choosing and Setting Up a Secure Browser
Picking a safe web browser is like picking a reliable car for a cross-country road trip; the sturdier, the better! Look for browsers that have strong security features, like frequent updates and good privacy controls. Some favorites include Mozilla Firefox, Google Chrome, and Brave. They come equipped with robust gears to navigate the web securely.
| Browser | What They Offer in Security |
|---|---|
| Mozilla Firefox | Frequent updates, strong privacy settings, extra tracking shields |
| Google Chrome | Consistent updates, safe browsing mode, sandboxing tech |
| Brave | Blocks ads, safeguards against fingerprinting, automatic HTTPS shifts |
For tricks on securing your browser, catch our handy guide on how to secure your browser.
Understanding HTTPS and Secure Websites
While browsing, it’s like keeping your conversations private. HTTPS is the magic spell that encrypts data between your device and the site, making eavesdropping tough. Always look for URLs starting with “https://” instead of “http://”—the padlock icon is your best buddy!
| HTTP | HTTPS |
|---|---|
| Data not locked up | Data locked up tight |
| No ID check | ID check and data wholeness |
| Easy prey for attackers | Beefed-up protection |
To dig deeper, check out the online shopping security tips.
Safe Downloading Practices
Grabbing files off the internet requires a bit of street smarts. Stick with these tips to stay sharp:
- Only download from well-known sites.
- Double-check the website and program before hitting “download.”
- Have antivirus protection scan your downloads (CISA).
- Avoid illegal downloads like cracked software or media.
If you came across a dodgy file, find out what’s next at signs of computer hack.
Ad Blockers and Security Extensions
Ad blockers and security extensions can make your online life less noisy and more secure by stopping nasty ads and pop-ups cold and dodging unwanted trackers. Here are some solid picks:
| Extension | What It Does |
|---|---|
| uBlock Origin | Blocks ads, kicks malware to the curb |
| HTTPS Everywhere | Auto-HTTPS conversion |
| Privacy Badger | Stops tracker snoopers |
Adding these tools can give your online safety a hefty boost.
Follow these rules for safer browsing and to reduce your chances of falling prey to online threats. For more handy tips, see how to create a strong password and how to adjust social media privacy settings.
Digital Security for Your Family
Keeping your family safe online requires doing some homework and having some solid tools to protect everyone and their gadgets.
Teaching Children About Online Safety
Kiddos need to get the lowdown on online safety nice and early. Here’s what to chat about with them:
- Guarding Personal Info: Make sure they get why spilling personal secrets online’s a no-go.
- Spotting Unfriendlies: Let them know some folks online ain’t there to play fair.
- Browsing Smart: Stick to websites that are on the up-and-up.
Use everyday examples they can relate to. Keep the conversation flowing about what’s happening online and what to do if something feels off.
Parental Controls and Monitoring Tools
Parental controls and monitoring tools are like having a parental third eye. These keep the bad stuff out and help you keep tabs on your kid’s digital hangouts.
| Tool | Feature | Benefit |
|---|---|---|
| Net Nanny | Web Filtering, App Blocking | All-rounder in parental controls |
| Qustodio | Screen Time Management, Activity Insights | Lets you see what’s what |
| Norton Family | Location Tracking, Time Oversight | Sturdy safety measures |
Getting these tools to work with your home gadgets is a game-changer. For a deep dive, check out secure home network setup.
Family Password Management Strategies
Nailing down your passwords can slam the door on any digital snoopers. Here’s the game plan:
- Grab a password manager to keep your passwords locked up tighter than Fort Knox.
- Go strong and diverse with your passwords; make them tough to crack (how to create strong password).
- Always turn on two-factor authentication if it’s an option.
Creating a Family Cybersecurity Plan
Getting everyone on board with a simple security plan covers a lot of bases. Make sure it includes:
Incident Response
What to do if something sketchy turns up:
- Speak Up: Tell the kids to hit you up with anything weird they spot, like emails from so-called princes.
- Quarantine the Device: If something ain’t right, pull the plug on the internet connection.
- Password Refresh: Give your passwords a makeover if you suspect they’ve been eyeballed.
- Call in Reinforcements: Serious mess-ups or hacking attempts need reporting to the big guns.
Regular Updates
Stay on it with updates for all gadgets. Fresh systems can stop trouble before it starts. Curious about why updates rock? Visit why software updates are important.
Education and Awareness
Keep the whole crew savvy about what’s hot (or not) in online safety. Stay in the loop with places like The Hacker News and Unsupervised Learning.
These tips can up your online game big time. Being clued-up and ready makes tackling digital hiccups a breeze.
Peek at more tips and guides, like how to secure cloud storage, social media privacy settings, and how to secure browser.
Conclusion:
So, you want to keep your digital gates secure, huh? Well, let’s get you started. Keeping the cyber baddies at bay is like guarding your house – gotta lock the doors and windows before trouble shows up. We’re talkin’ strong passwords, keeping your gadgets up-to-speed with updates, and side-eyeing sketchy links. These basics are your helmet and pads in the wild world of the web (CISA).
If I were you, I’d snag a password manager and switch on two-factor authentication. Trust me, more layers of security mean fewer sleepless nights.
Here’s what you oughta focus on:
- Password Security: Create strong passwords by jumbo-sizing them with a mix of letters, numbers, and symbols. Read our playbook for more tips.
- Software Updates: Don’t sleep on updates; they’re your digital vaccine. Miss one, and you could end up like the sorry folks in the Equifax breach of 2017 (TealTech).
- Email Vigilance: Phishing emails are like candy from strangers—just say no. Get wise with our email security tips.
To keep your personal details locked down, always practice safe browsing—yes, we mean with VPNs and taking control of those social media privacy settings. Our pieces on browsing safely and using public WiFi without paranoia are here to guide you.
Oh, and don’t skimp on protection; clothe your devices in the finest antivirus software and get busy with backup strategies. It’s like insurance, but for your bytes. Teach your family about this stuff too.
Build these habits, and you’ll hold the key to your own cyber fort. Stay sharp and shut down any virtual threat with a wink. Welcome to the online survival club!




